Microsoft Windows security uses SIDs for authentication. This number uniquely identifies accounts on a local computer. The account name can be changed, but the SID remains the same. When a computer joins a domain, the domain controller assigns it a Domain SID for authentication purposes.
Determine the Current User’s SID
Open a (DOS or PowerShell) command prompt and enter:
> whoami /user
This PowerShell one-liner works quickly too.
PS> [System.Security.Principal.WindowsIdentity]::GetCurrent().User.Value
Many web articles say to determine your SID, you should type “wmic useraccount domain, name, sid”. This will certainly work but if you are on a corporate domain, it can take a really long time to get results – and it will return every domain account!
Use PowerShell to Get User SID
Below is a quick script to get the SID of the current user:
PS> Get-LocalUser -Name $env:USERNAME | Select-Object sid
Alternatively, you can get the SID of a local system user:
PS> Get-LocalUser -Name 'User' | Select-Object sid
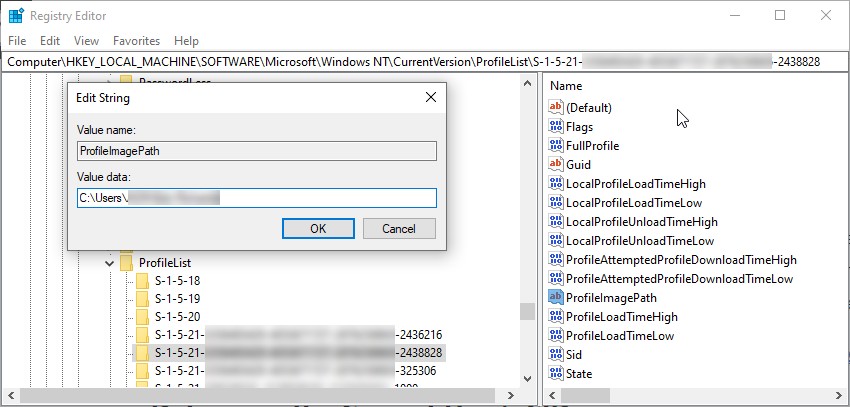
Manually Using Registry
- Open registry editor “regedit”.
- Navigate to “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList”
- Examine the “ProfileImagePath” key for each SID.
Well Know SIDs
Certain SIDs are well defined and present on all systems. Here is a Microsoft article on well known SIDs.
